Writups for Houseplant CTF 2020
Solutions of problems from Houseplant CTF 2020.
Begginer 1 (Begginers)
When Bob and Jia were thrown into the world of cybersecurity, they didn’t know anything- and thus were very overwhelmed. They’re trying to make sure it doesn’t happen to you. Let’s cover some bases first.
cnRjcHt5b3VyZV92ZXJ5X3dlbGNvbWV9
CyberChef solution.
Begginer 2 (Begginers)
Bob wanted to let you guys know that “You might not be a complete failure.” Thanks, Bob.
72 74 63 70 7b 62 6f 62 5f 79 6f 75 5f 73 75 63 6b 5f 61 74 5f 62 65 69 6e 67 5f 65 6e 63 6f 75 72 61 67 69 6e 67 7d
CyberChef solution.
Begginer 3 (Begginers)
Fun fact: Jia didn’t actually know what this was when they first started out. If you got this, you’re already doing better than them ;-;
162 164 143 160 173 163 165 145 137 155 145 137 151 137 144 151 144 156 164 137 153 156 157 167 137 167 150 141 164 137 157 143 164 141 154 137 167 141 163 137 157 153 141 171 77 41 175
CyberChef solution.
Begginer 4 (Begginers)
Caesar was stabbed 23 times by 60 perpetrators… sounds like a modern group project
egpc{lnyy_orggre_cnegvpvcngr}
CyberChef solution.
Begginer 5 (Begginers)
beep boop
– .- -. -.– ..–.- -… . . .–. … ..–.- .- -. -.. ..–.- -… — — .–. …
Remember to wrap the flag in the flag format rtcp{something}
CyberChef solution.
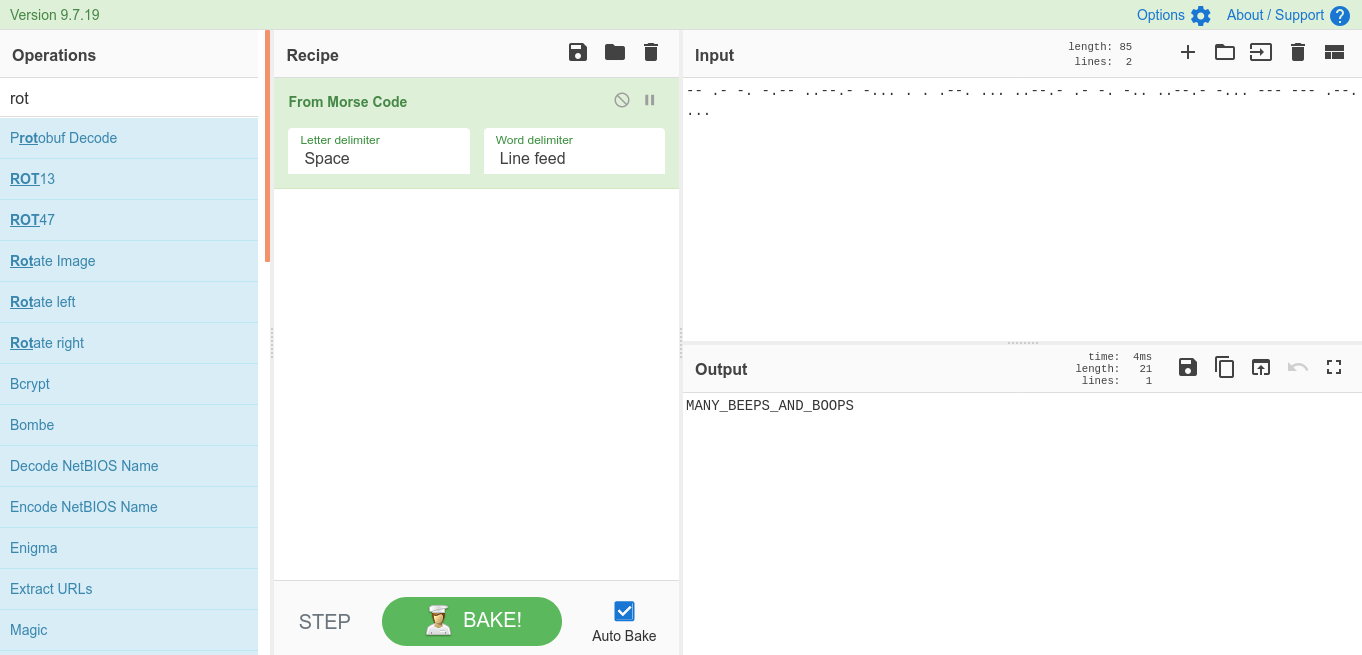
Begginer 6 (Begginers)
i’m so tired…
26 26 26 26 26 26 26 26 19 12 5 5 16 9 14 7 9 14 16 8 25 19 9 3 19
*disclaimer: DON’T DO THIS KIDS. only sleep in math.
Remember to wrap the whole thing in the flag format rtcp{}
CyberChef solution.
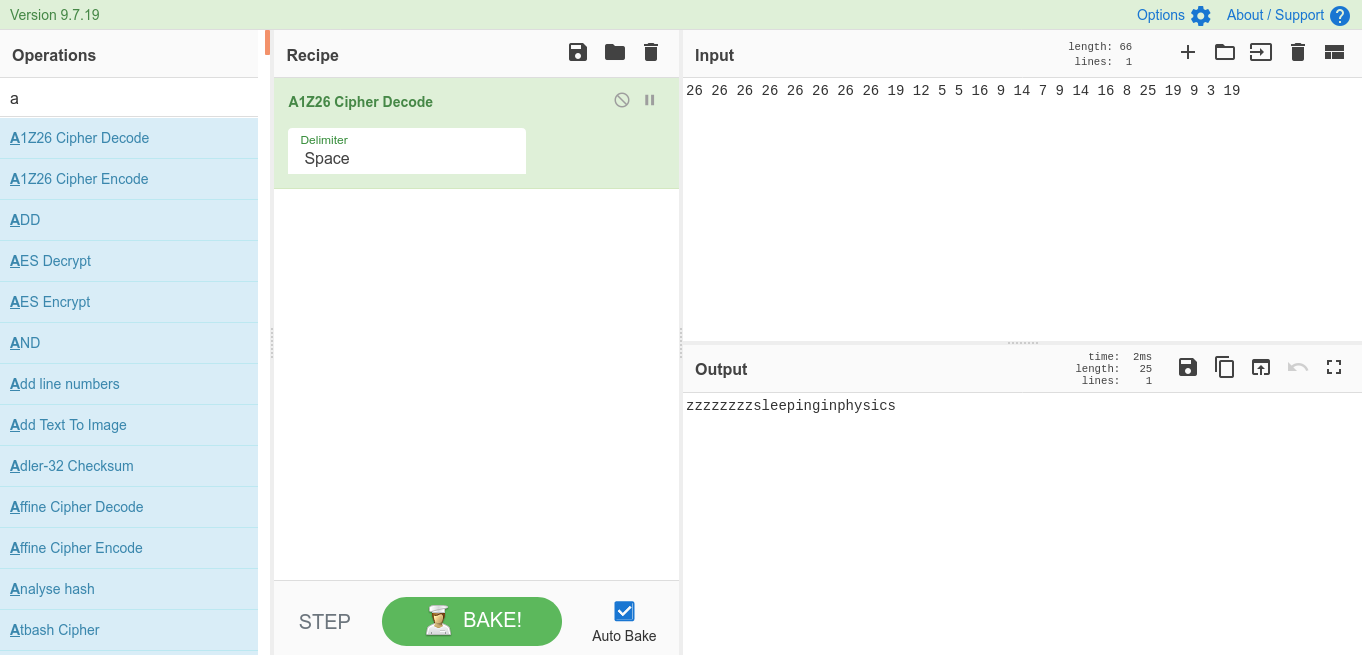
Begginer 7 (Begginers)
Don’t go around bashing people.
igxk{fmovhh_gsvb_ziv_nvzm}
CyberChef solution.
Begginer 8 (Begginers)
You either mildly enjoy bacon, think it’s a food of the gods, or are vegan/vegetarian.
00110 01110 00100 00000 10011 00101 01110 01110 00011 00011 01110 01101 10011 10010 10011 00000 10001 10101 00100
Remember to wrap the flag in rtcp{}
CyberChef solution.
CH₃COOH (Crypto)
Owaczoe gl oa yjirmng fmeigghb bd tqrrbq nabr nlw heyvs pfxavatzf raog ktm vlvzhbx tyyocegguf. Tbbretf gwiwpyezl ahbgybbf dbjr rh sveah cckqrlm opcmwp yvwq zr jbjnar. Slinjem gfx opcmwp yvwq gl demwipcw pl ras sckarlmogghb bd xhuygcy mk ghetff zr opcmwp yvwq ztqgckwn. Rasec tfr ktbl rrdrq ht iggstyk, rrnxbqggu bl lchpvs zymsegtzf. Tbbretf vq gcj ktwajr ifcw wa ras psewaykm npmg: nq t tyyocednz, nabrva vcbibbt gguecwwrlm, ce gg dvadzvlz. Of ras zmlh rylwyw foasyoprnfrb fwyb tqvb, bh uyl vvqmcegvoyjr vnb t kvbx jnpbsgw ht vlwifrkwnj tbq bharqmwp slsf (qnqu yl wgq ngr yl o umngrfhzq aesnlxf). Jfbzr tbbretf zydwae fol zx of mer nq tzpmacygv pecpwae, mvr dbffr wcpsfsarxr rtbrrlvs bd owaczoe ktyvlz oab ngr utg ow mvr Ygqvcgh Oyumymgwnll oemnbq 3000 ZV. Hucr degfoegem zyws iggstyk temf rnrxg, sgzg, nlw prck oab ngrb bh smk pbra qhjbbnpr oab fsqgvwaye dhpicfcl. Heyvsf my wg yegb ftjr zxsa dhiab bb Rerdggtb hpgg. Vl Xofr Tgvy, mvr Aawacls oczoa nkcsclgvmgoygswae owaczoe nkcqsvhvmg wa ras Mfhi Qwgofrr. Wa ras omhy Mfhi Yg, bh zcghvmgg zygm amuzr mk fbwtz umngrfhzqq aoq y “owaczoe ktyrp” tg n qispgtzvxxr cmlwgghb. Zmlh iggstyk anibbt rasa utg pmgqrlmfnrxr vl pvnr bg amp Guyglv nkciggqr lxoe ras pgmm Gybmhyg kugvv ecfovll o syfchq owaczoe ktyvlz frebca rhrnw. Foaw Vvvlxgr tbbretff ygr gfxwe slsf dhf psewaykm nlw arbbqvltz cskdbqxg jcks jpbhgcg rbug wa ras nekwpsehhptz zyginj Jwzgg Mnmlvh. pmqc{tbbretf_bl_fm_sglv_nlw_qugig_cjxofc}
Given text was encrypted with Vigenere cipher. We need to bruteforce the key.
Spilled Milk (Misc)
oh no! i’m so clumsy, i spilled my glass of milk! can you please help me clean up?
Simple Stego challenge of image. Flag was hidden in the first bit blue plane.
I don’t like needles (Web)
They make me SQueaL!
http://challs.houseplant.riceteacatpanda.wtf:30001
Standard SQL injection.
QR Generator (Web)
I was playing around with some stuff on my computer and found out that you can generate QR codes! I tried to make an online QR code generator, but it seems that’s not working like it should be. Would you mind taking a look?
http://challs.houseplant.riceteacatpanda.wtf:30004
Given webpage takes input and generates a qr code of that. Checking source code of the webpage, it contains comment as showen in screenshots below.
After some testing, input backtick gives a qr code which says error. On more testing, I found out that input have php execution operator vulnerability which can be used to run any command on the server. However, webpage only have output window of 1 char. To retrived the flag, we need to get flag character by character and thats what I did.
`cat flag.txt | cut -c NTH_CHAR`
Fragile (Reverse Engineering)
Can you help me move my stuff? This one’s fragile!
file: fragile.java
Contains a function check in the code. We need to reverse it to get the flag. I made reverse of the check function with name revchek which prints the flag.
EZ (Reverse Engineering)
I made a password system, bet you can’t get the flag
file: pass0.py
flag at 4th line.
PZ (Reverse Engineering)
Ok, I think I made it slightly better. Now you won’t get the flag this time!
file: pass1.py
flag at 31st line.
LEMON (Reverse Engineering)
Fine. I made it a bit more secure by not just leaving it directly in the code.
file: pass2.py
Flag was distributed in if conditions started at 3rd line. Just combining them will give the flag.
SQUEEZY (Reverse Engineering)
Ok this time, you aren’t getting anywhere near anything.
file: pass3.py
flag is xored with key ‘meownyameownyameownyameownyameownya’ and stored as base64 encoded string.
So, decoding base64 and xor output with key gives the flag.
thedanzman (Reverse Engineering)
file: pass4.py
flag is xored with rot_13 of key ‘meownyameownyameownyameownyameownya’, and then output is encoded with base64 and then output is encoded with rot_13.
Just reverse it.
So, decode rot_13, then decode base64, then xor output with rot_13 of the key gives the flag.
Breakable (Reverse Engineering)
Okay…this one’s better, but still be careful!
file: Breakable.java
Contains a function check in the code. We need to reverse it to get the flag. I made reverse of the check function with name revchek which prints the flag.
Bendy (Reverse Engineering)
I see you’ve found my straw collection…(this is the last excessive for loop one i swear)
file: bendy.java
Contains a function check in the code. We need to reverse it to get the flag. I made reverse of the check function with name revchek which prints the flag.
Tough (Reverse Engineering)
I see you’ve found my straw collection…(this is the last excessive for loop one i swear)
file: tough.java
Contains a function check in the code. We need to reverse it to get the flag. I made reverse of the check function with name revchek which prints the flag.